Vulnerability Assessments A Quick Guide
Vulnerability Assessments A Quick Guide
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of vulnerability assessment methods
Vulnerability Assessment Tools And Checklists Manageengine Vulnerability Manager Plus
Vulnerability Assessment Tools And Checklists Manageengine Vulnerability Manager Plus
Vulnerability Assessment Scanning Tools List 2018 Esecforte
Vulnerability Assessment Scanning Tools List 2018 Esecforte
How To Perform A Vulnerability Assessment A Step By Step Guide
How To Perform A Vulnerability Assessment A Step By Step Guide
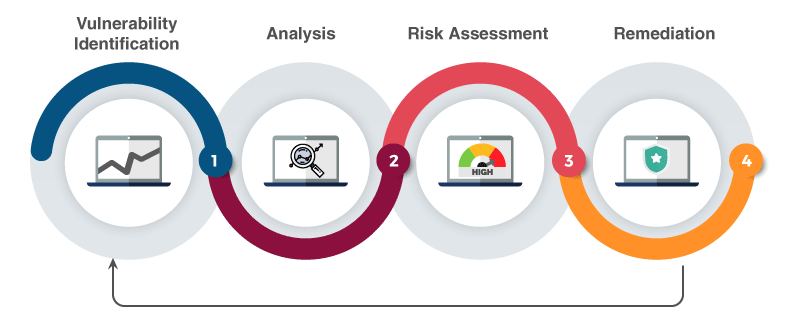
The Vulnerability Assessment Process Analysis Risk Assessment Remediation
The Vulnerability Assessment Process Analysis Risk Assessment Remediation
Network Vulnerability Assessment And Management Guide
Network Vulnerability Assessment And Management Guide
The Steps Of The Vulnerability Assessment Methodology Download Scientific Diagram
The Steps Of The Vulnerability Assessment Methodology Download Scientific Diagram
What Is Vulnerability Assessment Types And Process
What Is Vulnerability Assessment Types And Process
10 Best Vulnerability Assessment Tools And Techniques Olinux
10 Best Vulnerability Assessment Tools And Techniques Olinux
Sustainability Free Full Text Seismic Vulnerability Assessment Methodologies For Roadway
Sustainability Free Full Text Seismic Vulnerability Assessment Methodologies For Roadway
What Is Vulnerability Assessment Cybersecuriosity Professional Cyber Security Services
What Is Vulnerability Assessment Cybersecuriosity Professional Cyber Security Services
Vulnerability Assessments 4 Crucial Steps For Identifying Vulnerabilities In Your Business
Vulnerability Assessments 4 Crucial Steps For Identifying Vulnerabilities In Your Business
How Is Vulnerability Management Different From Vulnerability Assessment Kratikal Blogs
How Is Vulnerability Management Different From Vulnerability Assessment Kratikal Blogs
The Importance Of Vulnerability Assessment Types And Methodology Security Boulevard
The Importance Of Vulnerability Assessment Types And Methodology Security Boulevard
Top Vulnerability Assessment And Management Best Practices Sysdig
Top Vulnerability Assessment And Management Best Practices Sysdig
Vulnerability Assessment Methods Pdf Seismology Earthquakes
Vulnerability Assessment Methods Pdf Seismology Earthquakes
3 The Move Generic Framework Used For Vulnerability Assessment Download Scientific Diagram
3 The Move Generic Framework Used For Vulnerability Assessment Download Scientific Diagram
Vulnerability Assessment Services Crest Approved Cyphere
Vulnerability Assessment Services Crest Approved Cyphere
Vulnerability Assessment The First Step In Securing Your Business Cpi Solutions
Vulnerability Assessment The First Step In Securing Your Business Cpi Solutions
Vulnerability Assessment Tools Tool To Maintain Systems And Security
Vulnerability Assessment Tools Tool To Maintain Systems And Security
The Vulnerability Assessment Methodology Download Scientific Diagram
The Vulnerability Assessment Methodology Download Scientific Diagram
Vulnerability Assessment Best Practices How To Be One Step Ahead Of Attackers From
Vulnerability Assessment Best Practices How To Be One Step Ahead Of Attackers From
Creating A Vulnerability Management Strategy Zsecurity
Creating A Vulnerability Management Strategy Zsecurity
Schematic Of Vulnerability Assessment Methods Adapted From Hodgson Download Scientific Diagram
Schematic Of Vulnerability Assessment Methods Adapted From Hodgson Download Scientific Diagram
The Role Of Vulnerability Assessment And The Corresponding Download Scientific Diagram
The Role Of Vulnerability Assessment And The Corresponding Download Scientific Diagram
Vulnerability Assessment And Penetration Testing Ec Council Global Services Egs
Vulnerability Assessment And Penetration Testing Ec Council Global Services Egs
How To Perform A Network Vulnerability Assessment With Examples Purplesec
How To Perform A Network Vulnerability Assessment With Examples Purplesec
Risk Assessment And Vulnerability Analysis Sigma Earth
Risk Assessment And Vulnerability Analysis Sigma Earth
Vulnerability Assessment Definition Types And Importance
Vulnerability Assessment Definition Types And Importance