Top 9 File Integrity Monitoring Fim Best Practices Sysdig
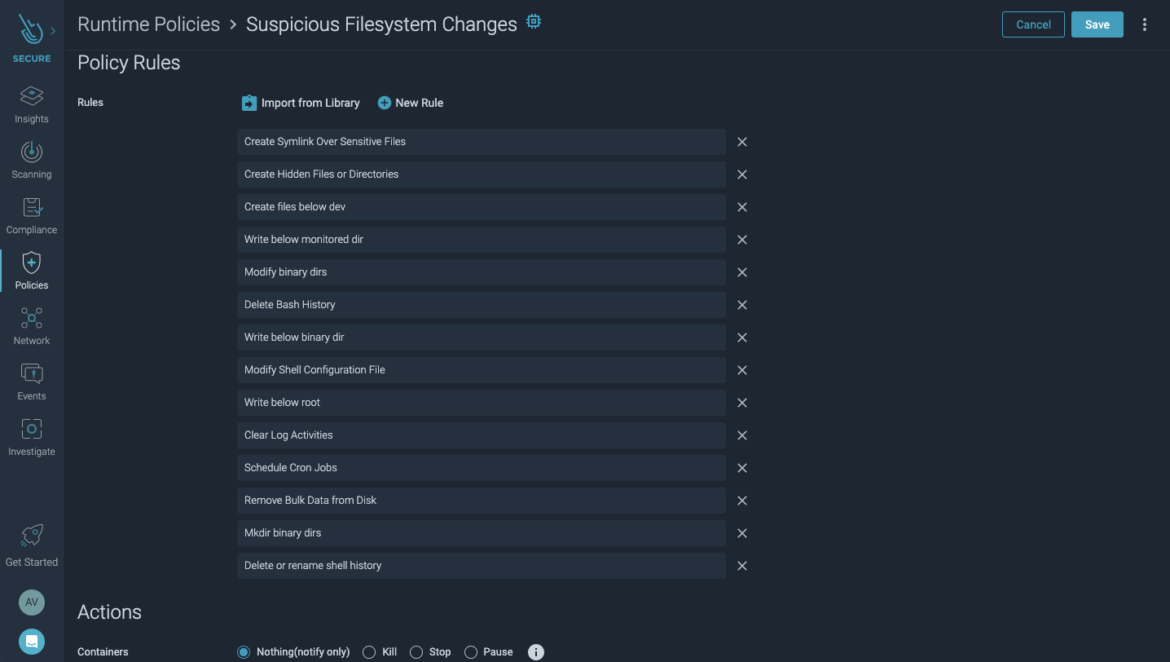
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of file integrity monitoring fim detect malware and active response to malware detectionagain
File Integrity Monitoring Fim Detect Malware And Active Response To Malware Detectionagain
File Integrity Monitoring Fim Detect Malware And Active Response To Malware Detectionagain
File Integrity Monitoring Fim Detect Malware And Active Response To Malware Detectionagain
File Integrity Monitoring Fim Detect Malware And Active Response To Malware Detectionagain
Fim What Is File Integrity Monitoring Guide Technologies
Fim What Is File Integrity Monitoring Guide Technologies
File Integrity Monitoring Software Fim Integrity Checker Solarwinds
File Integrity Monitoring Software Fim Integrity Checker Solarwinds
File Integrity Monitoring And Yara Malware Detection
File Integrity Monitoring And Yara Malware Detection
File Integrity Monitoring Software Fim Features And Benefits
File Integrity Monitoring Software Fim Features And Benefits
What Is File Integrity Monitoring Fim Why Do You Need It
What Is File Integrity Monitoring Fim Why Do You Need It
File Integrity Monitoring And Threat Detection Rules
File Integrity Monitoring And Threat Detection Rules
File Integrity Monitoring Software Fim Integrity Checker Solarwinds
File Integrity Monitoring Software Fim Integrity Checker Solarwinds
Top 5 Best File Integrity Monitoring For Enterprises Tek Tools
Top 5 Best File Integrity Monitoring For Enterprises Tek Tools
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
Essential Fim Must Haves A Quick Guide For Choosing A File Integrity Monitoring Solution File
Essential Fim Must Haves A Quick Guide For Choosing A File Integrity Monitoring Solution File
The Five Stages Of File Integrity Monitoring Fim Tripwire
The Five Stages Of File Integrity Monitoring Fim Tripwire
What Is File Integrity Monitoring Fim And Hows It Work Infosec Insights
What Is File Integrity Monitoring Fim And Hows It Work Infosec Insights
File Integrity Monitoring Fim Stealth Iss Group Inc Total Cyber Solutions
File Integrity Monitoring Fim Stealth Iss Group Inc Total Cyber Solutions
File Integrity Monitoring Fim For Ensuring Security And Compliance Arcon
File Integrity Monitoring Fim For Ensuring Security And Compliance Arcon
File Integrity Monitoring Fim Using Defender For Cloud To Comply With Pci Dss Requirement
File Integrity Monitoring Fim Using Defender For Cloud To Comply With Pci Dss Requirement
File Integrity Monitoring And Malware Analysis Services Mindfire
File Integrity Monitoring And Malware Analysis Services Mindfire
Understanding File Integrity Monitoring Fim In Cybersecurity By Bytesofinfosec System Weakness
Understanding File Integrity Monitoring Fim In Cybersecurity By Bytesofinfosec System Weakness
Best Practices Of File Integrity Monitoring Socvault
Best Practices Of File Integrity Monitoring Socvault
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
File Integrity Monitoring Fim O Que é E Por Que é Tão Importante
File Integrity Monitoring Fim O Que é E Por Que é Tão Importante
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
Top 9 File Integrity Monitoring Fim Best Practices Sysdig
Configure File Integrity Monitoring Fim Using Defender For Cloud And Ama Agent
Configure File Integrity Monitoring Fim Using Defender For Cloud And Ama Agent