Entropy Free Full Text Malicious Url Detection Based On Associative Classification
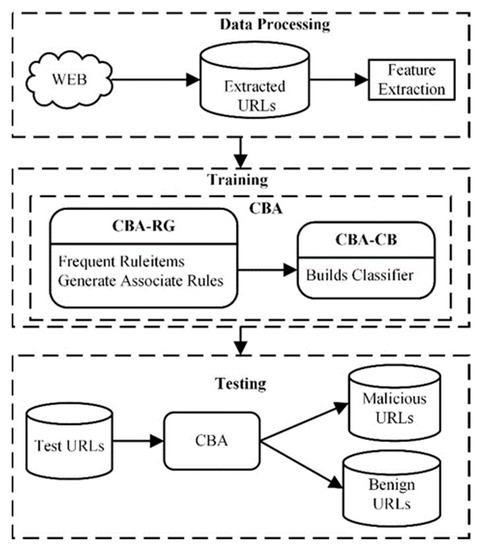
Entropy Free Full Text Malicious Url Detection Based On Associative Classification
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of applied sciences free full text cross method based analysis and classification of malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Classification And Analysis Of Malicious Code Detection
Applied Sciences Free Full Text Classification And Analysis Of Malicious Code Detection
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Applied Sciences Free Full Text Cross Method Based Analysis And Classification Of Malicious
Pdf Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls Extraction
Pdf Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls Extraction
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Cnn Based Image Classification Of Malicious Uavs
Applied Sciences Free Full Text Cnn Based Image Classification Of Malicious Uavs
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Cnn Based Image Classification Of Malicious Uavs
Applied Sciences Free Full Text Cnn Based Image Classification Of Malicious Uavs
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Table 1 From Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls
Table 1 From Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text Classification Of Malicious Urls By Cnn Model Based On
Applied Sciences Free Full Text An Lstm Based Deep Learning Approach For Classifying
Applied Sciences Free Full Text An Lstm Based Deep Learning Approach For Classifying
Pdf Classification And Analysis Of Malicious Code Detection Techniques Based On The Apt Attack
Pdf Classification And Analysis Of Malicious Code Detection Techniques Based On The Apt Attack
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Applied Sciences Free Full Text Malicious File Detection Method Using Machine Learning And
Classification Of Malicious Code Detection Methods Download Scientific Diagram
Classification Of Malicious Code Detection Methods Download Scientific Diagram
Applied Sciences Free Full Text Visualized Malware Multi Classification Framework Using Fine
Applied Sciences Free Full Text Visualized Malware Multi Classification Framework Using Fine
Applied Sciences Free Full Text Web Based Android Malicious Software Detection And
Applied Sciences Free Full Text Web Based Android Malicious Software Detection And
Entropy Free Full Text Malicious Url Detection Based On Associative Classification
Entropy Free Full Text Malicious Url Detection Based On Associative Classification
Table 1 From Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls
Table 1 From Cross Method Based Analysis And Classification Of Malicious Behavior By Api Calls
Symmetry Free Full Text Automatic Malicious Code Classification System Through Static
Symmetry Free Full Text Automatic Malicious Code Classification System Through Static
Pdf A New Classification Based Model For Malicious Pe Files Detection
Pdf A New Classification Based Model For Malicious Pe Files Detection
Pdf Classification Of Malicious Process Using High‐level Activity Based Dynamic Analysis
Pdf Classification Of Malicious Process Using High‐level Activity Based Dynamic Analysis
Pdf Malicious Code Classification Method Based On Deep Residual Network And Hybrid Attention
Pdf Malicious Code Classification Method Based On Deep Residual Network And Hybrid Attention
Classification And Protection Methods Of Malicious Software Tools
Classification And Protection Methods Of Malicious Software Tools
A Malicious Code Classification Method Based On Multiple Features And Feature Selection Eureka
A Malicious Code Classification Method Based On Multiple Features And Feature Selection Eureka
Pdf Classification And Identification Of Malicious Codes
Pdf Classification And Identification Of Malicious Codes
Figure 1 From Efficient Malicious Traffic Classification Methods Based On Semi Supervised
Figure 1 From Efficient Malicious Traffic Classification Methods Based On Semi Supervised