Cryptography Free Full Text Practical Architectures For Deployment Of Searchable Encryption
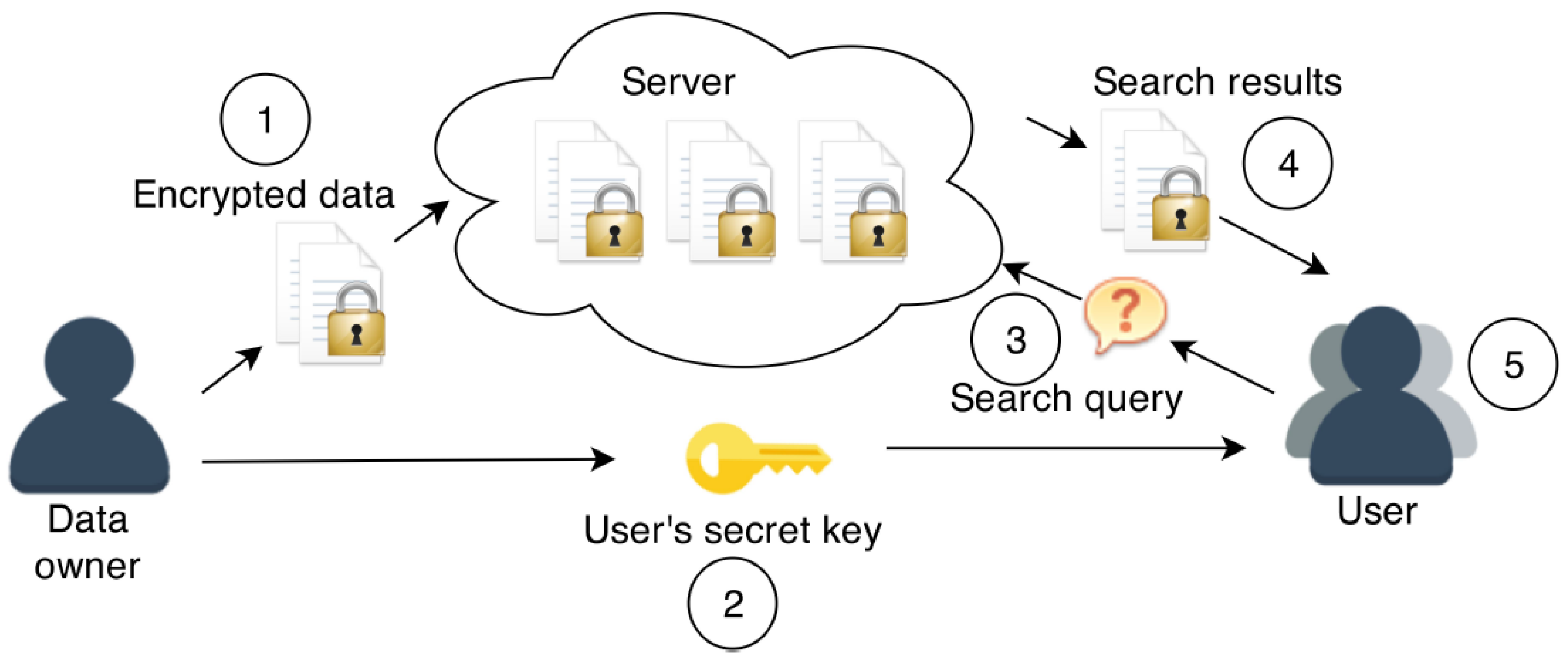
Cryptography Free Full Text Practical Architectures For Deployment Of Searchable Encryption
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of encryption in cloud security
Programming For Beginners Openssl Encrypt And Decrypt The Data Using Hot Sex Picture
Programming For Beginners Openssl Encrypt And Decrypt The Data Using Hot Sex Picture
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Cloud Security Tutorial Cloud Encryption Services Youtube
Cloud Security Tutorial Cloud Encryption Services Youtube
Top Encryption Strategies For Securing Your Sensitive Information In The Cloud Pyramid Systems
Top Encryption Strategies For Securing Your Sensitive Information In The Cloud Pyramid Systems
Encryption And Security In Cloud Computing Desklib
Encryption And Security In Cloud Computing Desklib
Cryptography Free Full Text Practical Architectures For Deployment Of Searchable Encryption
Cryptography Free Full Text Practical Architectures For Deployment Of Searchable Encryption
What Is Cloud Encryption Definition Importance Methods And Best Practices Spiceworks
What Is Cloud Encryption Definition Importance Methods And Best Practices Spiceworks
Cloud Encryption Step By Step How To Morpheus Multi Cloud Management And Devops Orchestration
Cloud Encryption Step By Step How To Morpheus Multi Cloud Management And Devops Orchestration
Cloud Security Encryption And Key Management Essentials
Cloud Security Encryption And Key Management Essentials
Cloud Encryption Software Encrypt Data Before Uploading To The Cloud
Cloud Encryption Software Encrypt Data Before Uploading To The Cloud
Data At Rest Encryption In The Cloud Explore Your Options Data Center Knowledge News And
Data At Rest Encryption In The Cloud Explore Your Options Data Center Knowledge News And
Trigyn Insights Role Of Encryption In Cloud Security
Trigyn Insights Role Of Encryption In Cloud Security
Technologies Free Full Text A Verifiable Fully Homomorphic Encryption Scheme For Cloud
Technologies Free Full Text A Verifiable Fully Homomorphic Encryption Scheme For Cloud
Advanced Encryption Techniques For Maximum Cloud Sharing Security Editorialge
Advanced Encryption Techniques For Maximum Cloud Sharing Security Editorialge
Premium Photo Digital Fortress Encrypted Cloud Data Security Concept Data Encryption Cloud
Premium Photo Digital Fortress Encrypted Cloud Data Security Concept Data Encryption Cloud
Data Security Encryption Approaches Deliver Varying Levels Of Multi Cloud Data Security
Data Security Encryption Approaches Deliver Varying Levels Of Multi Cloud Data Security
Premium Photo Cloud Computing Backup Cyber Security Fingerprint Identity Encryption Technology
Premium Photo Cloud Computing Backup Cyber Security Fingerprint Identity Encryption Technology
The Data Security Scheme For Cloud Computing Download Scientific Diagram
The Data Security Scheme For Cloud Computing Download Scientific Diagram
Quest Ce Que Le Cryptage De Données Définition Types Et Meilleures Pratiques Kinsta®
Quest Ce Que Le Cryptage De Données Définition Types Et Meilleures Pratiques Kinsta®
Proxy Encryption Encrypting With Public Key And Decrypt With Private Key Hot Sex Picture
Proxy Encryption Encrypting With Public Key And Decrypt With Private Key Hot Sex Picture
Applied Sciences Free Full Text Fully Homomorphic Encryption With Optimal Key Generation
Applied Sciences Free Full Text Fully Homomorphic Encryption With Optimal Key Generation
The Complete Cloud Encryption Guide Agency X Webflow Ecommerce Website Template
The Complete Cloud Encryption Guide Agency X Webflow Ecommerce Website Template
Data Encryption In The Cloud Types Examples And Software
Data Encryption In The Cloud Types Examples And Software
Cloud Encryption Everything About Encrypting Your Sensitive B
Cloud Encryption Everything About Encrypting Your Sensitive B
Aws Encryption Options For High Throughput And High Resilience Hot Sex Picture
Aws Encryption Options For High Throughput And High Resilience Hot Sex Picture