Cryptography Free Full Text A New Hybrid Automated Security Framework To Cloud Storage System
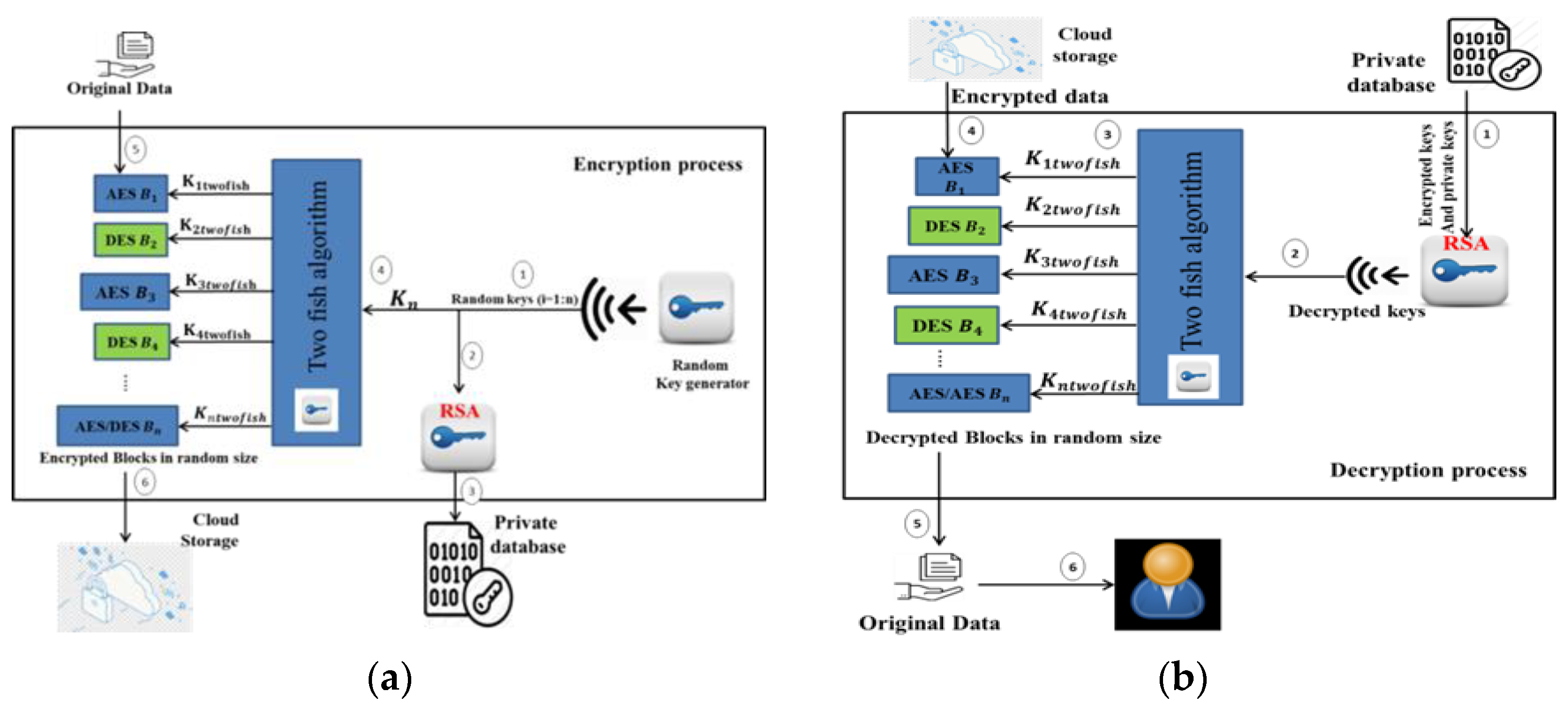
Cryptography Free Full Text A New Hybrid Automated Security Framework To Cloud Storage System
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of pdf hybrid data encryption technique for data security in cloud computing
Pdf Hybrid Data Encryption Technique For Data Security In Cloud Computing
Pdf Hybrid Data Encryption Technique For Data Security In Cloud Computing
How Hybrid Cryptography Secures Data In Cloud Computing
How Hybrid Cryptography Secures Data In Cloud Computing
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Secure File Storage In Cloud Computing Using Hybrid Cryptography Algorithm Semantic Scholar
Secure File Storage In Cloud Computing Using Hybrid Cryptography Algorithm Semantic Scholar
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Electronics Free Full Text Hybrid Aes Ecc Model For The Security Of Data Over Cloud Storage
Hybrid Cryptography Implementation Of A System Capable Of Encryption And Decryption Of
Hybrid Cryptography Implementation Of A System Capable Of Encryption And Decryption Of
Cryptography Free Full Text A New Hybrid Automated Security Framework To Cloud Storage System
Cryptography Free Full Text A New Hybrid Automated Security Framework To Cloud Storage System
Pdf A New Hybrid Data Encryption And Decryption Technique To Enhance Data Security In
Pdf A New Hybrid Data Encryption And Decryption Technique To Enhance Data Security In
Data Encryption In The Cloud Types Examples And Software
Data Encryption In The Cloud Types Examples And Software
Symmetry Free Full Text Encryption Techniques For Smart Systems Data Security Offloaded To
Symmetry Free Full Text Encryption Techniques For Smart Systems Data Security Offloaded To
Pdf Enhancing The Data Security In Cloud By Implementing Hybrid Rsa And Aes Encryption Algorithm
Pdf Enhancing The Data Security In Cloud By Implementing Hybrid Rsa And Aes Encryption Algorithm
Hybrid Cloud Security 5 Key Steps To Securing Cloud Environments Customer Centric Product
Hybrid Cloud Security 5 Key Steps To Securing Cloud Environments Customer Centric Product
The Data Security Scheme For Cloud Computing Download Scientific Diagram
The Data Security Scheme For Cloud Computing Download Scientific Diagram
Hybrid Cryptosystem Zend Crypt Zend Framework Docs
Hybrid Cryptosystem Zend Crypt Zend Framework Docs
Technologies Free Full Text A Verifiable Fully Homomorphic Encryption Scheme For Cloud
Technologies Free Full Text A Verifiable Fully Homomorphic Encryption Scheme For Cloud
Figure 1 From An Architecture For Data Security In Cloud Computing Semantic Scholar
Figure 1 From An Architecture For Data Security In Cloud Computing Semantic Scholar
Types Of Encryption 5 Encryption Algorithms And How To Choose The Right One Security Boulevard
Types Of Encryption 5 Encryption Algorithms And How To Choose The Right One Security Boulevard
Top 10 Types Of Security Software For Your Business Mytechmag
Top 10 Types Of Security Software For Your Business Mytechmag
Enhancing Cloud Security With A Two Step Cryptography Technique Help Net Security
Enhancing Cloud Security With A Two Step Cryptography Technique Help Net Security
Advanced Encryption Techniques For Data Science Applications In The Cloud
Advanced Encryption Techniques For Data Science Applications In The Cloud
Cloud Computing Data Center Multi Cloud Hybrid Cloud Information Storage Cyber Security
Cloud Computing Data Center Multi Cloud Hybrid Cloud Information Storage Cyber Security
Data Security In Cloud Trends In Cloud Security Cloud Computing
Data Security In Cloud Trends In Cloud Security Cloud Computing
What Is The Difference Between Encryption And Tokenization Which Is Better For Data Security
What Is The Difference Between Encryption And Tokenization Which Is Better For Data Security
Cryptographic Keys 101 What They Are And How They Secure Data Hashed Out By The Ssl Store™
Cryptographic Keys 101 What They Are And How They Secure Data Hashed Out By The Ssl Store™
The Most Effective Data Encryption Techniques A Step By Step Guide
The Most Effective Data Encryption Techniques A Step By Step Guide
Architecture Of The Search Over Encrypted Cloud Data Download Scientific Diagram
Architecture Of The Search Over Encrypted Cloud Data Download Scientific Diagram
Premium Photo Hybrid Office Data Security With Remote Encryption
Premium Photo Hybrid Office Data Security With Remote Encryption
Premium Ai Image Conceptual Cyber Security Encryption Technique For Data Generative Ai
Premium Ai Image Conceptual Cyber Security Encryption Technique For Data Generative Ai
What Is Encryption Definition Types And More Proofpoint Us
What Is Encryption Definition Types And More Proofpoint Us
What Is Asymmetric Encryption And How Does It Work Infosec Insights
What Is Asymmetric Encryption And How Does It Work Infosec Insights
Data Encryption Standard Des All You Need To Know Techfunnel
Data Encryption Standard Des All You Need To Know Techfunnel