5 Steps For Implementing It Security Controls What To Do And How To Do It
5 Steps For Implementing It Security Controls What To Do And How To Do It
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of security controls implementation overview diagram
Approaches To Information Security Implementation Geeksforgeeks
Approaches To Information Security Implementation Geeksforgeeks
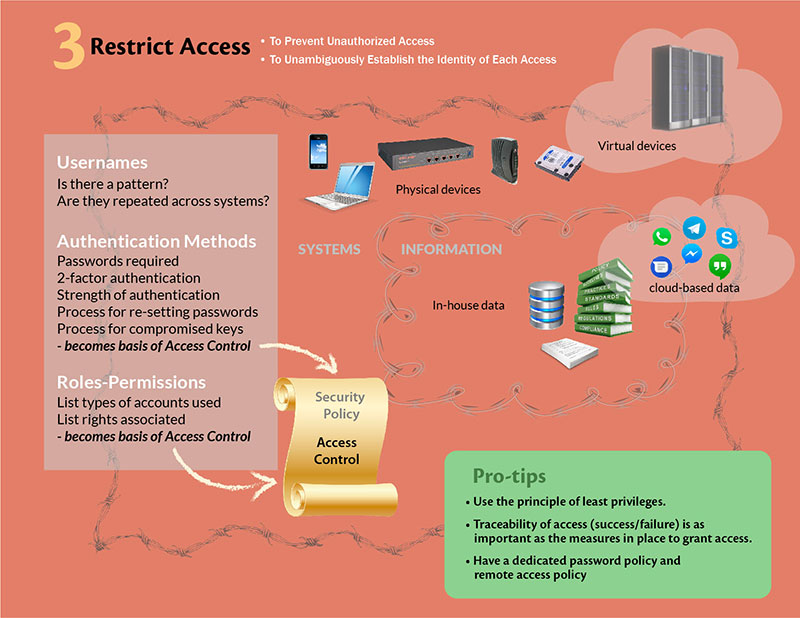
Technology Implementation Of Security Controls Template
Technology Implementation Of Security Controls Template
Implementation Of Security Controls Resources Part 1 Youtube
Implementation Of Security Controls Resources Part 1 Youtube
Sex Distribution Of Cases And Controls Download Scientific Diagram
Sex Distribution Of Cases And Controls Download Scientific Diagram
Information Security Controls In Healthcare Iquasar Cyber
Information Security Controls In Healthcare Iquasar Cyber
The Security Operating Model A Strategic Approach For Building A More Secure Organization
The Security Operating Model A Strategic Approach For Building A More Secure Organization
5 Steps For Implementing It Security Controls What To Do And How To Do It
5 Steps For Implementing It Security Controls What To Do And How To Do It
Nist Cybersecurity Framework Guide 2022 Core Implementation Profile Hot Sex Picture
Nist Cybersecurity Framework Guide 2022 Core Implementation Profile Hot Sex Picture
Electronic Technology Division Cybersecurity Systems Program Us Army Engineering And
Electronic Technology Division Cybersecurity Systems Program Us Army Engineering And
Cybersecurity Policies And Procedures Yokogawa Electric Corporation
Cybersecurity Policies And Procedures Yokogawa Electric Corporation
Nist Cybersecurity Framework Guide Core Implementation Profile Hot Sex Picture
Nist Cybersecurity Framework Guide Core Implementation Profile Hot Sex Picture
Czym Są Cis Critical Security Controls Implementation Groups Security Bez Tabu
Czym Są Cis Critical Security Controls Implementation Groups Security Bez Tabu
Cybersecurity Risk Minimization Method Improve Your Security Valerity
Cybersecurity Risk Minimization Method Improve Your Security Valerity
The 5 Cis Controls You Should Implement First Cso Online
The 5 Cis Controls You Should Implement First Cso Online
Information Security Management Iso 27001 Implementation Roadmap
Information Security Management Iso 27001 Implementation Roadmap
Cybersecurity Frameworks — Types Strategies Implementation And Benefits Ape Europe
Cybersecurity Frameworks — Types Strategies Implementation And Benefits Ape Europe
Information Security Program Implementation Guide Nist Summary
Information Security Program Implementation Guide Nist Summary
The 3 Types Of Security Controls Expert Explains Purplesec 2022
The 3 Types Of Security Controls Expert Explains Purplesec 2022
The 20 Critical Security Controls From Framework To Operational To Implementation Youtube
The 20 Critical Security Controls From Framework To Operational To Implementation Youtube
5 Steps For Implementing It Security Controls What To Do And How To Do It
5 Steps For Implementing It Security Controls What To Do And How To Do It
Overview Of The Nist Cybersecurity Framework One Critical Aspect For Compliance Proper
Overview Of The Nist Cybersecurity Framework One Critical Aspect For Compliance Proper
Aligning Metrics To Security Controls Frameworks Panaseer
Aligning Metrics To Security Controls Frameworks Panaseer
How To Develop And Implement A Network Security Plan
How To Develop And Implement A Network Security Plan