100 Days Of Devops — Day 8 Introduction To Aws Security Token Servicests By Prashant Lakhera
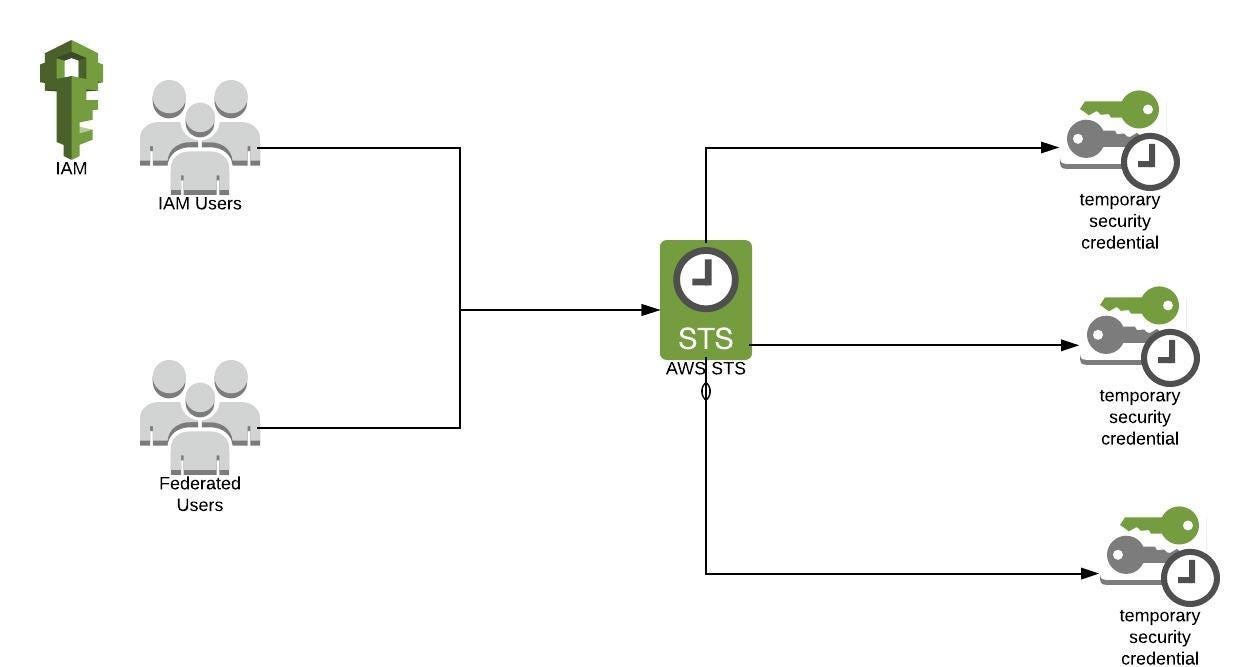
100 Days Of Devops — Day 8 Introduction To Aws Security Token Servicests By Prashant Lakhera
If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please Contact Us for abuse. We will follow up your report/abuse within 24 hours.
Related Images of 7 security identity and compliance aws youtube
Aws Security And Compliance For Enterprises Youtube
Aws Security And Compliance For Enterprises Youtube
Aws Security Hub Working With Security Standards And Controls To Improve Your Security Posture
Aws Security Hub Working With Security Standards And Controls To Improve Your Security Posture
Aws Certification And Training Aws Certified Developer Associate Exam Prep
Aws Certification And Training Aws Certified Developer Associate Exam Prep
100 Days Of Devops — Day 8 Introduction To Aws Security Token Servicests By Prashant Lakhera
100 Days Of Devops — Day 8 Introduction To Aws Security Token Servicests By Prashant Lakhera
Continuous Compliance Workflow For Infrastructure As Code Part 2 Aws Devops Blog
Continuous Compliance Workflow For Infrastructure As Code Part 2 Aws Devops Blog
How To Protect My Id Best Protection From Identity Theft Youtube
How To Protect My Id Best Protection From Identity Theft Youtube
The Crucial Difference Between It Security And It Compliance
The Crucial Difference Between It Security And It Compliance
Aws Identity And Access Management Access Analyzer Amazon Web Services
Aws Identity And Access Management Access Analyzer Amazon Web Services
7 Reasons Identity And Access Management Is Important
7 Reasons Identity And Access Management Is Important
Sinisa Medic On Linkedin Automate Your Sap Security And Focus On Your Core Business
Sinisa Medic On Linkedin Automate Your Sap Security And Focus On Your Core Business
7 Security Issues You Can Find With The Help Of Siem February 23 2023 Online Event
7 Security Issues You Can Find With The Help Of Siem February 23 2023 Online Event
Now Offering 247 Security Soc To Clients Newswerx Framewerx
Now Offering 247 Security Soc To Clients Newswerx Framewerx
How To Prevent Aws Encrypted Ransomware Cyberattacks F5
How To Prevent Aws Encrypted Ransomware Cyberattacks F5
Building A Strong Information Security Team At Dangote Group
Building A Strong Information Security Team At Dangote Group
Society Of Corporate Compliance And Ethics Scce On Linkedin As Part Of Corporate Compliance
Society Of Corporate Compliance And Ethics Scce On Linkedin As Part Of Corporate Compliance
How To Pronounce Sex 7 Pronunciation Ocean Youtube
How To Pronounce Sex 7 Pronunciation Ocean Youtube
Sattrix Information Security On Linkedin Sattrix Managedsoc Soc
Sattrix Information Security On Linkedin Sattrix Managedsoc Soc
Identity Relationships And Sex Education Unit Teaching Resources
Identity Relationships And Sex Education Unit Teaching Resources
American Technology Services Llc On Linkedin Cloud Security Best Practices By American
American Technology Services Llc On Linkedin Cloud Security Best Practices By American
Icl Soc Identification And Response To Cyber Threats Services
Icl Soc Identification And Response To Cyber Threats Services
247 Security Services The Nonstop Protection You Need
247 Security Services The Nonstop Protection You Need
Ppt Gdpr Certification Process Unveiled Powerpoint Presentation Free Download Id12531338
Ppt Gdpr Certification Process Unveiled Powerpoint Presentation Free Download Id12531338
247 Protection The Role Of Critical Security Services In Safeguarding Businesses
247 Protection The Role Of Critical Security Services In Safeguarding Businesses
The Ultimate Guide To Oral Sex 7 Key Mistakes Men Make Youtube
The Ultimate Guide To Oral Sex 7 Key Mistakes Men Make Youtube